The primary focus of Information Security is implementing the following 3 goals to an organizations information or assets:
Confidentiality – restricting access to information by implementing authentication or encryption
Integrity – protecting information from unauthorized modification or destruction
Availability – making sure an asset or resource is available when required
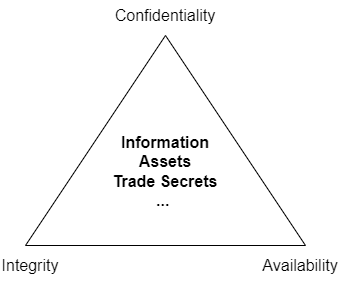
Our mission here is to protect information from unauthorized access, unauthorized modification and making sure it is available when required
Frameworks
There are quite a few frameworks out there that deal with information security:
ISO 2700 Family
The most well known and internationally recognized framework when it comes to information security. This framework is filled with a large amount of standards, the most important are:
ISO/IEC 27001 – Information Security Management Systems – Requirements
ISO/IEC 27002 – Code of Practice for Information Security Management
ISO/IEC 27005 – Information Security Risk Management
ISO/IEC 27017 – Code of practice for information security controls for cloud computing services
ISO/IEC 27018 – Code of practice for controls to protect personally identifiable information processed in public cloud computing services
TISAX (Trusted Information Security Assessment Exchange)
Based on ISO 27000 and mostly used in the Automotive Industriy
BSI Grundschutz
Established by the Federal Office for Information Security (BSI) in Germany, BSI Grundschutz is often implemented in the branches of Government and/or Public Service in Germany. BSI Grundschutz can be audited according to ISO 27001 however these certifications are not being handed out by an accredited certification body. This means that outside of germany, the recognition of the certificate may be limited.
All the Components of the BSI Grundschutz are provided free of charge an can provide a benefit even if you are working with ISO 27001 or TISAX. Grundschutz ist based on these 4 models:
- BSI-Standard 200-1: Information Security Management Systems (ISMS)
- BSI-Standard 200-2: IT-Grundschutz-Methodology
- BSI-Standard 200-3: Risk Analysis based on IT-Grundschutz
- BSI-Standard 200-4: Business Continuity Management
 2024@robinward.org
2024@robinward.org Web
Web